What is a cipher suite?
A cipher suite is a set of information that helps determine how your web server will communicate secure data over HTTPS.
A web server uses certain protocols and algorithms to determine how it will secure your web traffic. These are the ingredients of a secure connection. A cipher suite is essentially a list of those ingredients.
A cipher suite looks like this:
Why cipher suites are important
The security level of your HTTPS traffic (the safety of your data and the data of your users) depends on which cipher suites your web server uses.
The compatibility of your HTTPS traffic (who will see errors, warnings or experience other issues) depends on the cipher suites your web server uses.
The performance of your HTTPS traffic (how fast users see your pages – page speed) depends on the cipher suites your web server uses.
Just to sum that up, your website uses cipher suites to determine…
- How secure it is
- Who can see it
- How it is displayed in browsers
- How fast users can see your website
I bet you are more interested in cipher suites now than when you first started this article!
A cipher suite is like a recipe
If I were to make banana bread, there would be certain items and ingredients required.
Just as a recipe requires specific ingredients, a successful secured connection requires specific things as well. A cipher suite is simply a list of ingredients that your web server has standing by, ready to be used.
Those “ingredients” are algorithms and protocols instead of food items. A webmaster doesn’t really need to know what all those ingredients are or what they do, but they should know what cipher suites exist on their web server and how they were chosen.
Let’s dig a little deeper.
Cipher suites
Cipher suites are a combination of cryptographic algorithms used to provide security for HTTPS traffic.

Here is an example of a cipher suite:
Using the above cipher suite, let’s see what those ingredients are.
ECDHE is the key exchange algorithm
ECDSA is the authentication algorithm
AES128 is the bulk encryption algorithm
SHA256 is the MAC algorithm
These algorithms are part of what is used to create and secure your HTTPS traffic.
Your web server has a list of cipher suites if it is using HTTPS.
The list will look something like this:
If you look closely, you will see that this is simply a list of cipher suites separated by colons (:).
What do cipher suites do?
Cipher suites are an integral part of how your website functions over HTTPS. They list the various algorithms that cover the spectrum of the data security process (key exchange, authentication, encryption, etc.).
Since there are so many computers with different versions of operating systems, using different versions of different browsers, there needs to be a way to accommodate all possible combinations.
This is where cipher suites come to the rescue. When making a connection, a web server and browser can compare their lists of cipher suites, see if they are compatible, and if so determine which cipher suite to use. This is an important part of the “handshake” that happens when a server and browser make a connection.
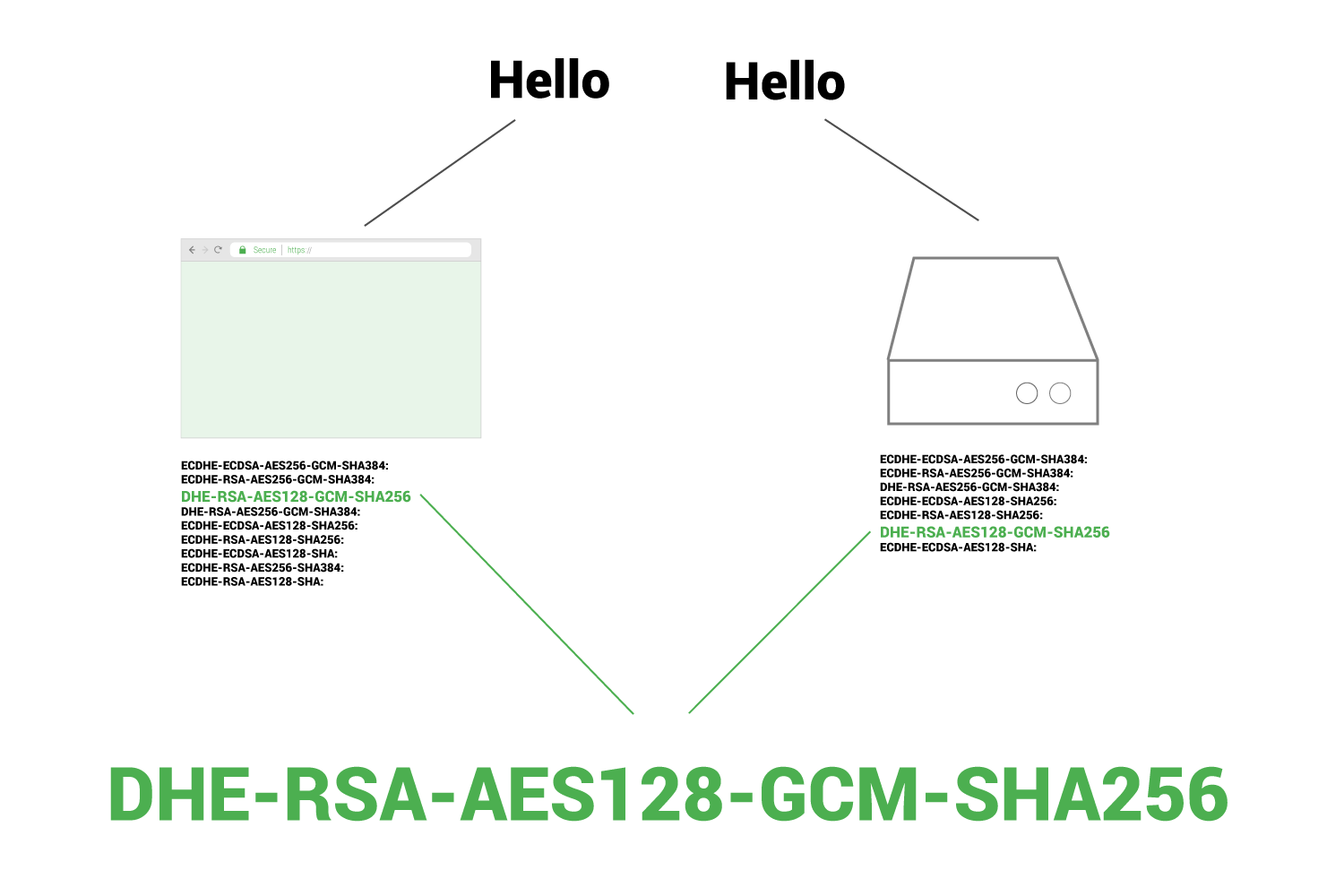
During the handshake, the client and server exchange a prioritized list of cipher suites so they can determine the cipher suite that is best supported by both.
The list of ciphers suites on your web server determines how secure, compatible, and fast your HTTPS traffic will be
Knowing which cipher suites your web server is using is important.
The list of cipher suites a web server uses affects many issues that webmasters care about (security, speed, compatibility, etc.) and a well-informed webmaster can improve their site by adjusting what cipher suites are being used.
If you can’t list the ciphers suites your web server uses (or know where they came from) you are likely missing out on some optimizations that could help improve your site’s security and speed while making it more compatible with more users.
Choosing cipher suites
There are many cipher suites to choose from. For this reason, a web server will have many listed cipher suites. Often a collection of a dozen or more cipher suites will be listed and this helps ensure compatibility.
Each web server or browser may not support certain ciphers suites listed by the other, so there needs to be a choice. The two sides seeking secure data can then compare their lists of cipher suites and decide on which they will use to move forward.
These sets of cipher suites help ensure that the most secure cipher suite will be used to get the best security.
Compatibility of cipher suites

One great way to determine what cipher suite sets are good for you is to decide what type of users you have, and what type of technology they use.
Mozilla (the makers of the Firefox browser) has a great resource for recommended configurations for security, which includes sets of cipher suites.
They break them down into three categories.
Modern compatibility
For services that don’t need backward compatibility… configuration is compatible with Firefox 27, Chrome 30, IE 11 on Windows 7, Edge, Opera 17, Safari 9, Android 5.0, and Java 8.
The cipher suites listed under this category are the latest and greatest. These can be used by sites that do not rely on or expect users who have older machines or browsers. A tech blog, for example, would likely have no issue using the modern cipher suites as their readers are probably tech savvy and keep things up to date. The modern compatibility set is the best set of cipher suites to use if you are able to do so.
Intermediate compatibility
For services that don’t need compatibility with legacy clients (mostly WinXP), but still need to support a wide range of clients, this configuration is recommended. It is compatible with Firefox 1, Chrome 1, IE 7, Opera 5 and Safari 1.
Considered a default set of cipher suites, these will be appropriate for most websites.
Old backward compatibility
This is the old ciphersuite that works with all clients back to Windows XP/IE6. It should be used as a last resort only.
This set of cipher suites is not recommended but does work for websites that rely on users likely to have older machines, older operating systems, and older software.
How to find out what cipher suites your web server is using
If you are not aware of what cipher suites your web server supports currently (they are listed in the config files of the web server) there is an easy way to determine what cipher suites your web server can support.
That is the free Qualys SSL Test.
This will test your overall HTTPS situation, and it reports and lists specifically which cipher suites are being used. Here is a screenshot of the cipher suite results from that test:
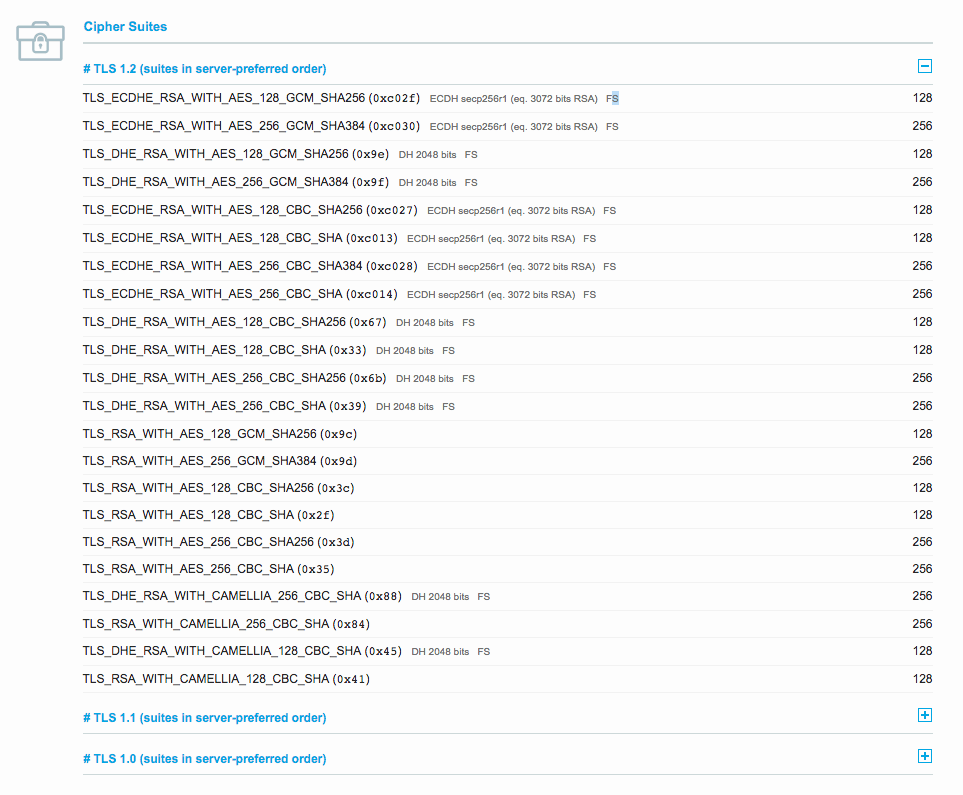
This report will tell you not only what cipher suites your server uses, but it also reports the order of preference of those cipher suites.
Anyone with a website using HTTPS should run their site through this test as it will tell you many things about your security set up.
Cipher suites maintenance
Cipher suites are only part of the process that makes a webpage secure. They are one of many security configurations that you can choose to make your website more secure and compatible. It is worth knowing if your cipher suites are up to date.
They tend to be forgotten or not known about at all.
Most cipher suite sets can use some optimization. It is a good practice to check your HTTPS configuration every few months. Knowing if you have the right cipher suites on your server is a great place to start.
See more of our HTTPS articles
 Table of Contents
Table of Contents